Effectively communicating cybersecurity risks to non-technical stakeholders is a critical skill for cybersecurity professionals. Often, these stakeholders include senior executives, board members, business managers, and clients who may lack deep technical understanding but hold decision-making authority.
Clear, concise, and relatable communication bridges the gap between technical jargon and business impact, enabling informed decisions that support organisational security.
Key Principles for Effective Communication
Consider these core practices for presenting risks in ways that stakeholders can easily understand and act upon:
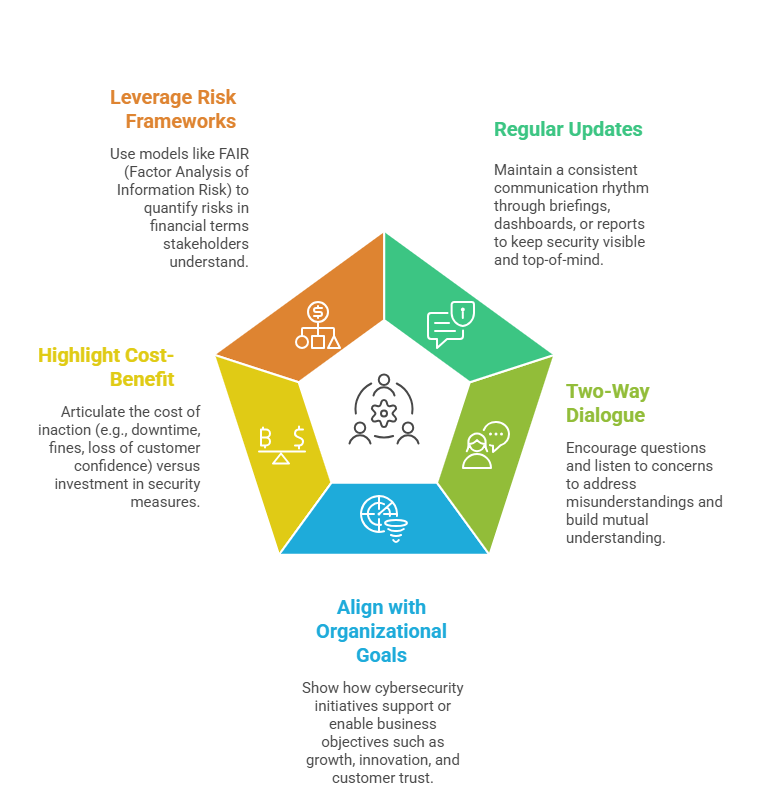
1. Use Plain Language: Avoid technical terms and acronyms. Explain cybersecurity risks in simple, everyday language.
2. Focus on Business Impact: Emphasise how risks affect business operations, financial health, reputation, and regulatory compliance. Decision-makers prioritise business continuity and risk reduction.
3. Provide Clear Context: Frame risks within the organization’s strategic goals and operational realities to create relevance and urgency.
4. Visualize Data: Utilize charts, graphs, and infographics to illustrate risk levels, trends, and potential impact clearly. Visual aids foster quicker comprehension.
5. Be Honest and Balanced: Share both strengths and weaknesses. Acknowledge current protections and gaps transparently to build trust.
6. Tell Stories: Use real-world examples, anonymised case studies, or scenarios to make abstract risks concrete and relatable. Stories help emotionally and intellectually engage stakeholders.
7. Tailor the Message: Customise communication based on the audience. Executives prefer concise summaries and business implications, while compliance officers seek details and evidence.
Strategies for Engaging Stakeholders
Common Challenges and Solutions
Bridging the technical-business gap is essential for securing support, resources, and trust. Highlighted here are effective methods to explain cybersecurity risks, their impacts, and mitigation strategies:
1. Technical Jargon Barrier: Overcome through training and preparing communications adaptable to non-technical audiences.
2. Risk Misinterpretation: Clarify probabilities and impacts to avoid alarmism or complacency. Use contextualized risk ratings.
3. Engagement Fatigue: Keep messages focused, relevant, and avoid information overload. Prioritize critical updates.
4. Cultural Resistance: Foster a security-aware culture by linking cybersecurity responsibility to everyone’s roles and successes.
Benefits of Effective Risk Communication
1. Builds organisational trust and credibility in security teams.
2. Secures executive support and resources for cybersecurity initiatives.
3. Improves cross-department collaboration on risk mitigation.
4. Enables proactive rather than reactive security posture.
Class Sessions
Sales Campaign

We have a sales campaign on our promoted courses and products. You can purchase 1 products at a discounted price up to 15% discount.