Footprinting is a critical phase in cybersecurity and ethical hacking, focusing on gathering vital information about a target organization’s network and infrastructure.
Through various techniques such as DNS lookup, WHOIS queries, website analysis, and metadata scrutiny, security professionals and attackers alike can identify vulnerabilities, map network structures, and develop targeted attack or defense strategies.
DNS Lookup Techniques
DNS (Domain Name System) lookup is one of the primary tools for footprinting, providing detailed information about DNS records associated with a domain.
1. A Record Lookup: Resolves domain names to IP addresses, revealing the IP addresses of web servers and other resources.
2. MX Record Lookup: Identifies mail servers associated with the domain, which can be targets for social engineering or phishing attacks.
3. NS Record Lookup: Fetches the authoritative name servers for the domain, exposing the DNS infrastructure and possible targets for DNS cache poisoning.
4. TXT Record Lookup: Retrieves textual data, often used for email authentication protocols like SPF, DKIM, and DMARC, but also potentially revealing internal policies or vulnerabilities.
5. Reverse DNS Lookup: Maps IP addresses back to domain names, useful for identifying related systems and infrastructure.
Tools such as nslookup, dig, and host are frequently used for DNS lookups, providing raw data or detailed reports about DNS configurations.
WHOIS Queries
WHOIS is a protocol used to query databases for registered domain information. It reveals details like domain registrant, registration and expiry dates, contact information, and registrar details.
This information can be exploited for social engineering, phishing, or to identify responsible parties for further attack planning. WHOIS data helps in identifying internal contacts, company ownership, or possible weak points in domain management.
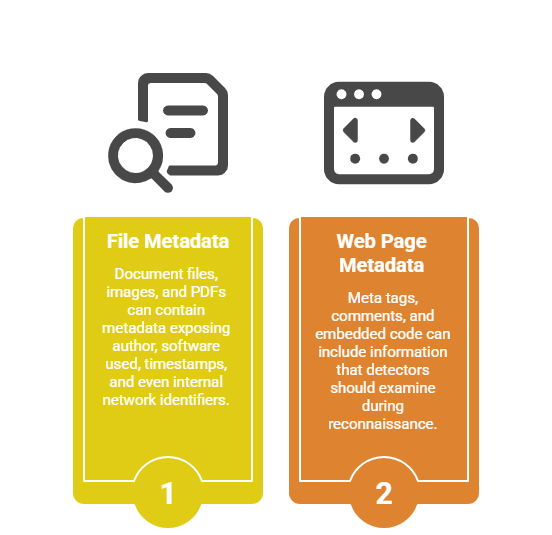
Website & Metadata Analysis
Website content, metadata, and server information can reveal insights that may be exploited if not properly secured. Here are the main approaches used to gather this information:
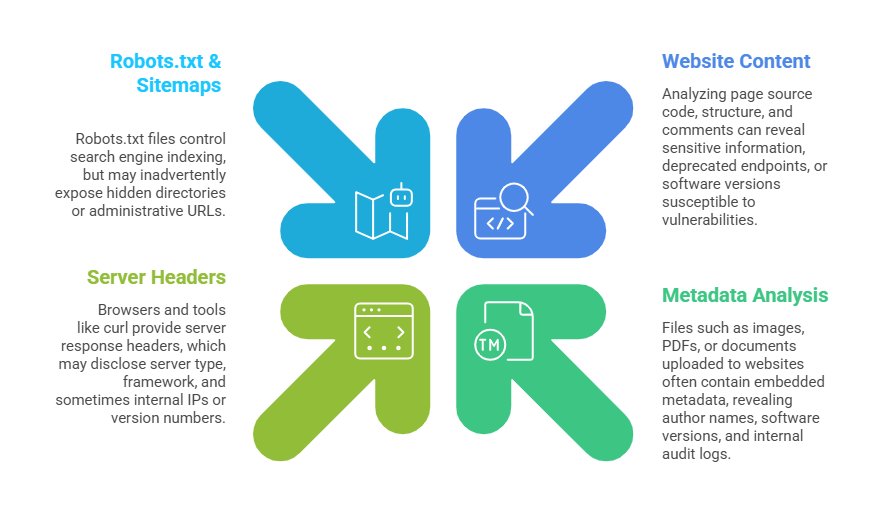
Understanding how domains and their subcomponents are structured is key to uncovering potential security weaknesses. Here are the main approaches used in identifying networks and subdomains:
1. Subdomain Enumeration: Tools like Sublist3r or dnsrecon perform brute-force or dictionary attacks to find subdomains, which may host less-secure or internal services.
2. Zone Transfer (AXFR): If misconfigured, DNS servers allow zone transfers, revealing entire domain and DNS record details—valuable for mapping the entire network structure.
3. Enumerating Internal IPs: Techniques such as traceroute and IP range scans uncover internal infrastructure and interconnectivity.
Tools and Commands
To map a target’s digital presence, investigators often use command-line and automation tools that gather DNS and domain insights. Outlined here are the primary tools and commands used in this process:
dig, nslookup, whois, theHarvester, dnsrecon, and sublist3r are widely used for footprinting.
Commands like dig example.com ANY request all DNS records for a domain to provide a comprehensive view.
Zone transfer attempts (dig AXFR) can be highly informative but only work if misconfigured.