Passwords remain a primary line of defense in securing digital accounts and systems. Password security focuses on creating and managing passwords that effectively protect against unauthorised access through various attacks, such as brute force, guessing, or credential stuffing.
Key components of password security include password strength, the use of cryptographic hashing for safe storage, and awareness of common weaknesses that jeopardise password effectiveness. Understanding these principles is essential for both users and security professionals to maintain secure authentication practices.
Password Strength
Strong authentication begins with well-constructed passwords that resist common attack techniques. Here are the essential factors that determine how secure a password truly is:
1. Length: The longer the password, the exponentially harder it is to crack. Passwords should generally have at least 12 to 16 characters. Length offers greater protection than simply adding complexity.
2. Complexity: A strong password includes a mix of uppercase and lowercase letters, numbers, and special characters. This increases the number of possible permutations, slowing down brute force attacks.
3. Unpredictability: Avoid common words, phrases, or personal information such as names, birthdays, or simple patterns (e.g., “123456”). Unpredictable strings resist dictionary and guessing attacks.
4. Uniqueness: Every account should have a distinct password to prevent a breach in one system from compromising others.
Password Hashing Concepts
Why Hashing? Passwords stored in plaintext are a severe security risk. Hashing transforms a password into a fixed-length output (hash) that cannot be easily reversed, protecting stored credentials even if databases are breached.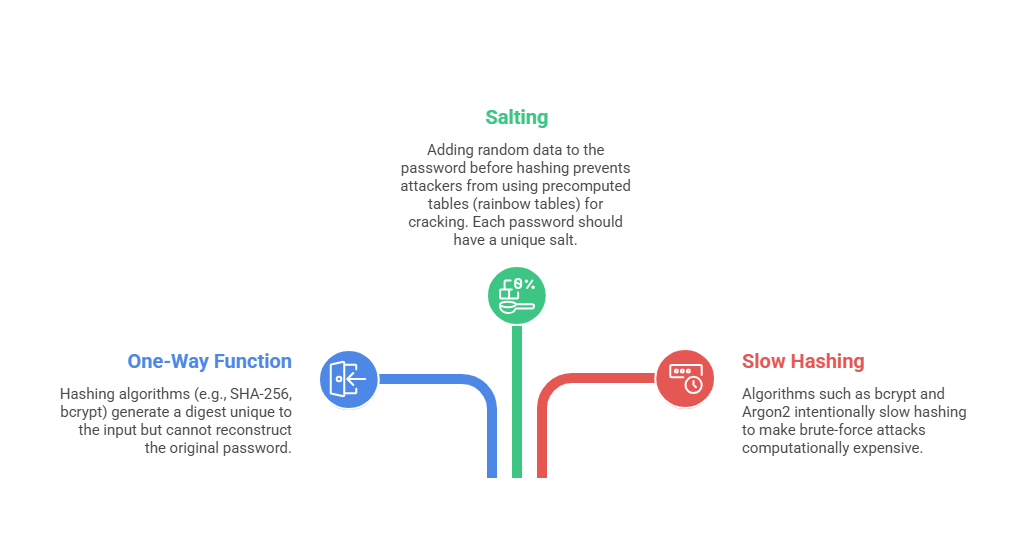
Common Password Weaknesses
1. Short Length: Passwords shorter than 8 characters are significantly easier for automated tools to crack quickly.
2. Simple Composition: Passwords like “password123” or “qwerty” are predictably guessable.
3. Reuse of Passwords: Using the same password across multiple accounts endangers all linked services if one is compromised.
4. Storing Passwords Insecurely: Storing passwords in plaintext files, spreadsheets, or improperly hashed formats exposes accounts to data breaches.
5. Social Engineering Risks: Passwords based on personal information can be guessed by attackers using information from social media or public records.
Best Practices for Password Security
Effective password security depends on consistent behaviors that minimize exposure to attacks. The following recommendations highlight essential steps for building safer authentication routines:
1. Use Long Passphrases: Memorable phrases or random word combinations that are long yet easy to recall.
2. Employ Password Managers: Secure vaults generate, store, and autofill complex, unique passwords for each account.
3. Enable Multi-Factor Authentication (MFA): Adds a non-password verification step, greatly increasing security.
4. Regularly Update Passwords: Change passwords periodically and immediately after a suspected breach.
5. Educate Users: Train users about phishing and the risks of weak passwords.
