Ethical hacking is a professional and authorized practice where cybersecurity experts intentionally probe computer systems, networks, or applications to identify vulnerabilities and security weaknesses.
Unlike malicious hackers who exploit these weaknesses for illegal or harmful purposes, ethical hackers operate with permission from the system owner to improve security.
Their goal is to simulate real-world cyberattacks to understand potential threats and help organizations strengthen defenses before attackers can exploit them.
Purpose of Ethical Hacking
The core purpose of ethical hacking is to enhance an organization’s cybersecurity posture by proactively identifying vulnerabilities and risks. By mimicking the tactics of malicious hackers, ethical hackers can:
1. Discover exploitable security flaws in systems, networks, and applications.
2. Test the effectiveness of security controls, such as firewalls and intrusion detection systems.
3. Ensure compliance with legal and industry security standards.
4. Provide actionable insights to help organizations remediate risks and improve security policies.
5. Educate stakeholders on potential threats and best security practices.
Scope of Ethical Hacking
The scope of ethical hacking can vary significantly based on organizational needs and agreed parameters, but generally includes: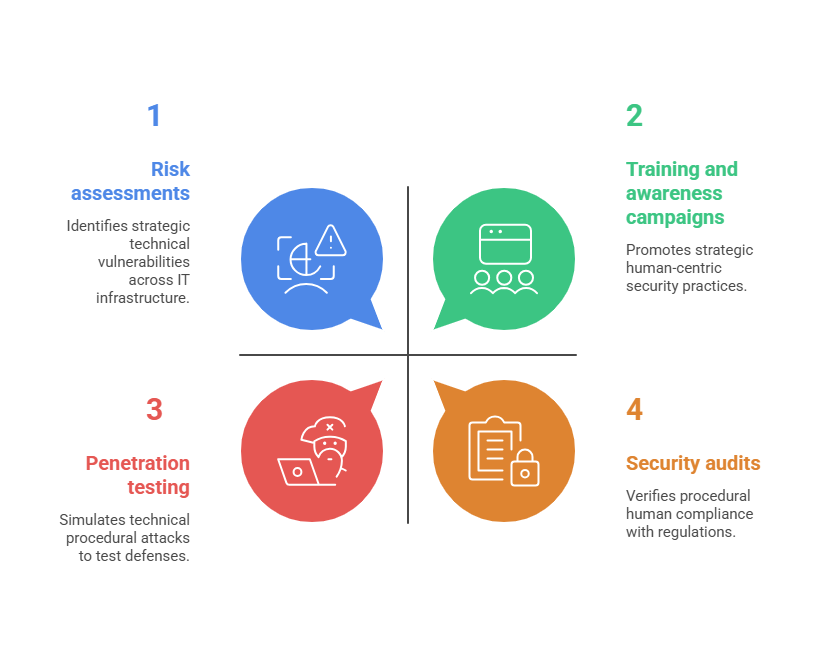 Ethical hacking thus spans technical, procedural, and human elements of cybersecurity.
Ethical hacking thus spans technical, procedural, and human elements of cybersecurity.
Limitations of Ethical Hacking
While ethical hacking plays a vital role in cybersecurity, it has inherent limitations:
1. Organizational Readiness: Without the capability or will to act on findings, ethical hacking’s value diminishes.
2. Defined Scope: Testing is limited to what’s contractually and legally permissible, which may exclude some vulnerabilities.
3. Legal and Regulatory Constraints: Ethical hackers must navigate complex laws and regulations to avoid unauthorized activities.
4. Technical Skill Requirements: Effective ethical hacking demands a wide-ranging skill set, and deficiencies in knowledge can limit penetration depth.
5. Resource Constraints: Time, budget, and computing power limitations may restrict the thoroughness of assessments.
6. Potential Risks: Testing can inadvertently cause data corruption or system disruptions if not carefully managed.
