Legal and ethical considerations form the foundation of responsible ethical hacking. Ethical hackers operate within strict legal boundaries and follow ethical guidelines to protect organizations while legally assessing their security.
Understanding and adhering to relevant laws, obtaining proper permissions, and conducting responsible disclosure are essential to avoid legal repercussions and maintain trust.
Legal Frameworks and Cyber Laws
Ethical hackers must be aware of the laws that govern cybersecurity and hacking activities. Key legal principles include:
1. Authorization: Ethical hacking requires formal permission from the system owner before any security testing begins. Unauthorized access is illegal, even with good intentions.
2. Computer Fraud and Abuse Acts: Many countries have laws that criminalize unauthorized computer access, data theft, and damage to systems (e.g., the U.S. Computer Fraud and Abuse Act - CFAA).
3. Data Protection Regulations: Laws like GDPR (Europe), HIPAA (Healthcare), and CCPA (California) impose strict controls on how sensitive data must be handled and protected.
4. Intellectual Property Rights: Ethical hackers must not violate copyrights, patents, or intellectual property while testing systems.
Adherence to these laws protects ethical hackers from prosecution and ensures organizational compliance with regulations.
Permissions and Scope of Work
Clear permissions and scope definition are fundamental to lawful ethical hacking:
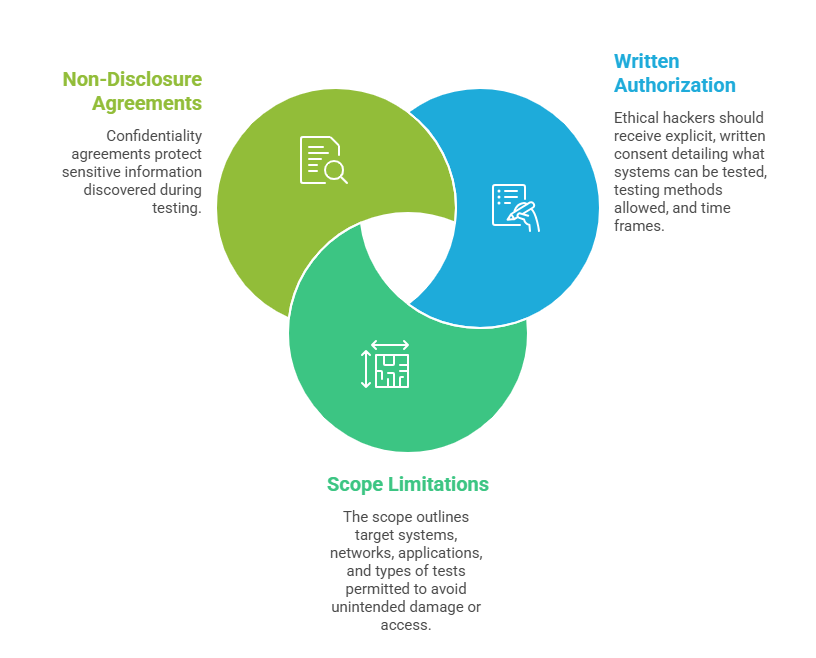
This contractually defined scope establishes trust and sets expectations between ethical hackers and clients.
Responsible Disclosure
When vulnerabilities are found, ethical hackers must follow responsible disclosure guidelines to report issues safely and constructively:
1. Timely Reporting: Report vulnerabilities promptly to authorized stakeholders without publicly disclosing them.
2. Cooperation: Work with the organization to provide detailed information to understand and reproduce the issue.
3. No Exploitation: Avoid exploiting vulnerabilities for personal gain or malicious intent.
4. Public Disclosure: Only with the organization’s consent, vulnerabilities may be disclosed publicly to raise awareness and encourage mitigation.
Responsible disclosure balances transparency with security and helps improve overall cybersecurity without causing harm.
Ethical Principles
Beyond laws, ethical hackers adhere to professional codes of conduct:
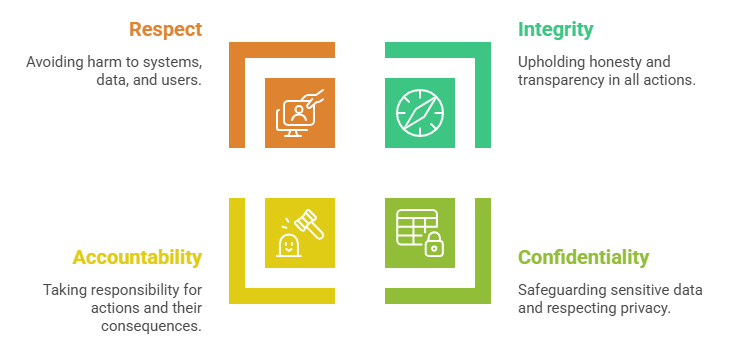
These principles guide ethical hackers in maintaining professionalism and trust.
