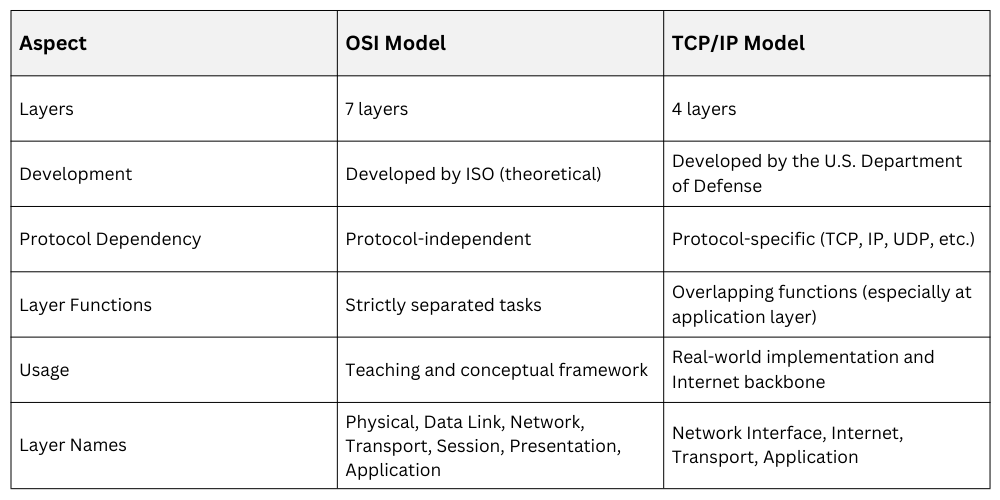
Networking protocols are essential for enabling communication between devices. Two foundational models that describe how data communication occurs in networks are the OSI (Open Systems Interconnection) model and the TCP/IP (Transmission Control Protocol/Internet Protocol) model.
While both use layered approaches to explain network functions, they differ in structure, implementation, and practical use. Understanding these models provides clarity on how data travels through networks and helps in troubleshooting and designing network systems.
OSI Model
The OSI model is a conceptual framework that divides network communication into seven distinct layers. Each layer performs specific tasks and communicates with the layers directly above and below it.
The OSI model is protocol-independent, meaning it can work with various network protocols and technologies. It is widely used as a teaching tool and for network analysis.
The Seven Layers of the OSI Model are:
Layer 1: Physical Layer – Deals with the physical transmission of data over hardware like cables, switches, and electrical signals.
Layer 2: Data Link Layer – Responsible for node-to-node data transfer and error detection/correction between directly connected devices. Includes MAC addressing.
Layer 3: Network Layer – Manages logical addressing and routing of data packets across multiple networks using IP addresses.
Layer 4: Transport Layer – Ensures reliable data delivery, manages flow control, and error recovery. TCP and UDP function here.
Layer 5: Session Layer – Establishes, manages, and terminates sessions or connections between devices.
Layer 6: Presentation Layer – Formats and translates data, including encryption and compression, ensuring data is in a readable format.
Layer 7: Application Layer – Interfaces directly with user applications and provides network services like HTTP, FTP, and SMTP.
TCP/IP Model
The TCP/IP model is a practical and widely implemented protocol suite primarily used on the Internet. Unlike the OSI’s seven layers, TCP/IP has four layers that combine certain OSI functions for efficiency and simplicity.
TCP/IP is protocol-dependent, meaning its layers are defined by standard protocols.
The Four Layers of the TCP/IP Model are:
1. Network Interface Layer (Link Layer): Combines OSI’s Physical and Data Link layers, enabling hardware addressing and physical transmission.
2. Internet Layer: Corresponds to OSI’s Network layer; responsible for addressing, packaging, and routing data via IP.
3. Transport Layer: Handles end-to-end communication, reliability, and error correction (TCP is the primary protocol here).
4. Application Layer: Encompasses OSI’s Session, Presentation, and Application layers; handles all higher-level protocols and user interactions.
Key Differences Between OSI and TCP/IP Models
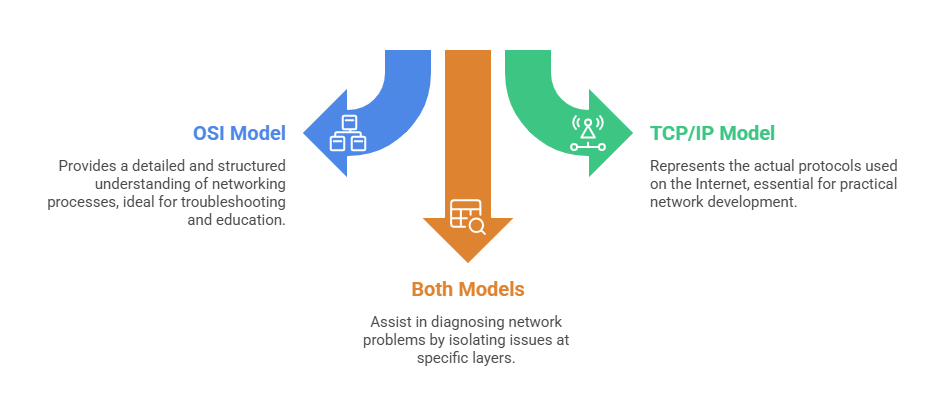
Importance and Application
Class Sessions
Sales Campaign

We have a sales campaign on our promoted courses and products. You can purchase 1 products at a discounted price up to 15% discount.
