Accurate and clear documentation of cybersecurity findings is essential for effective incident response, risk management, and future prevention strategies. Proper documentation ensures that all relevant facts and actions are recorded, enabling stakeholders to understand the scope of issues, evaluate the impact, and plan corrective measures.
In addition, thorough documentation supports compliance with legal and regulatory requirements and provides evidence during audits or investigations.
Importance of Clear and Factual Reporting
These points demonstrate the importance of structured reporting for legal, operational, and compliance purposes:
1. Provides Transparency: Clear documentation helps all stakeholders understand what vulnerabilities, threats, or incidents have been identified.
2. Supports Decision-Making: Accurate reports enable management to prioritize remediation efforts based on risk levels and impact.
3. Facilitates Follow-up Actions: Well-structured records guide incident response teams in mitigation, recovery, and lessons learned.
4. Ensures Legal and Regulatory Compliance: Many standards and laws mandate detailed reporting of security incidents, breaches, and vulnerabilities.
5. Serves as Evidence: Documentation can be critical in legal proceedings, audits, or insurance claims.
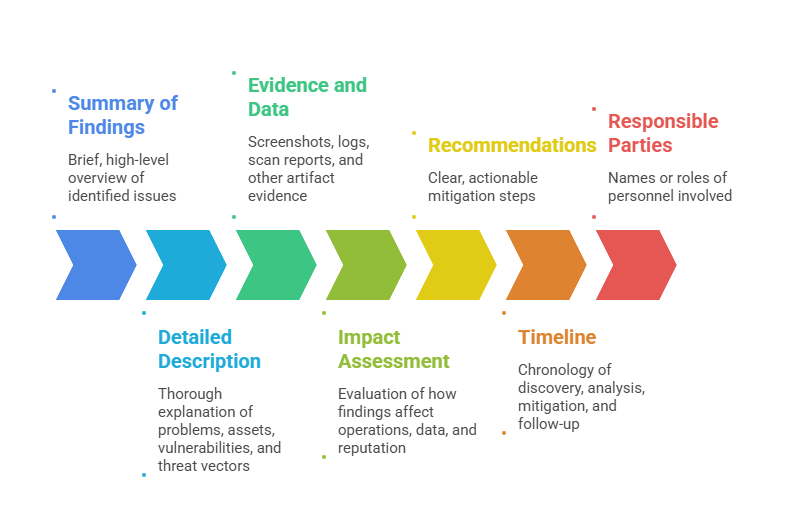
Key Elements of Documentation
Best Practices in Documentation
Maintaining proper documentation is essential for both operational efficiency and compliance. Consider these best practices to ensure reports are precise, understandable, and secure:
1. Maintain consistent formatting and terminology for clarity.
2. Use simple language free of ambiguity to ensure understanding by technical and non-technical stakeholders.
3. Record factual, unopinionated observations; avoid assumptions.
4. Link findings with supporting evidence, such as logs or screenshots.
5. Keep documentation secure, with controlled access, especially if sensitive information is involved.
6. Regularly review and update reports to reflect new findings or changes in status.
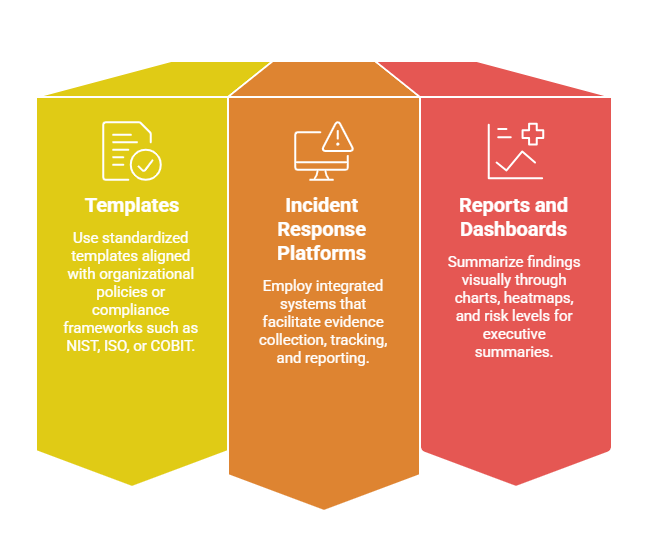
Tools and Formats for Documentation
Final Tips
1. Be objective and precise.
2. Ensure all data is verifiable, and source attribution is clear.
3. Document both successful and unsuccessful attempts at mitigation.
4. Foster a culture of transparency and continuous improvement.