Service and version enumeration is a vital stage in cybersecurity and ethical hacking, where the goal is to gather detailed information about the active services running on a target system or network, including their specific versions.
This process helps security professionals identify potential vulnerabilities associated with outdated or misconfigured software. By understanding exactly which services are exposed and their versions, organisations can prioritise patching and mitigation efforts to reduce their attack surface.
Service Enumeration
Service enumeration involves probing open ports on a target system to gather information about the services listening on those ports, such as HTTP, FTP, SSH, SMTP, and more.
It aims to identify the precise software and version numbers running, along with server configurations and security settings. This information is crucial because vulnerabilities are often version-specific—knowing the software version helps predict potential exploits.
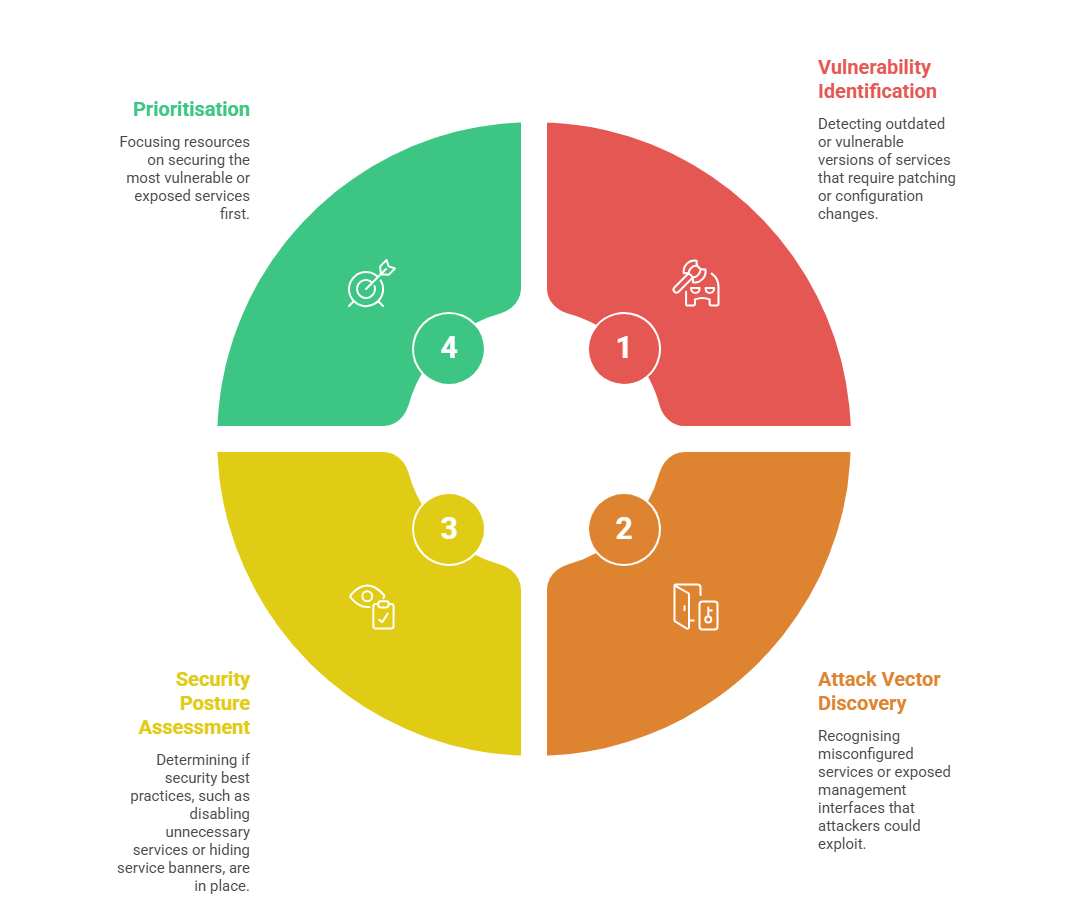
Importance of Service Enumeration
Evaluating active services helps organisations understand their security posture and operational gaps. The points that follow summarise why service enumeration is a crucial activity:
How Service & Version Enumeration Works
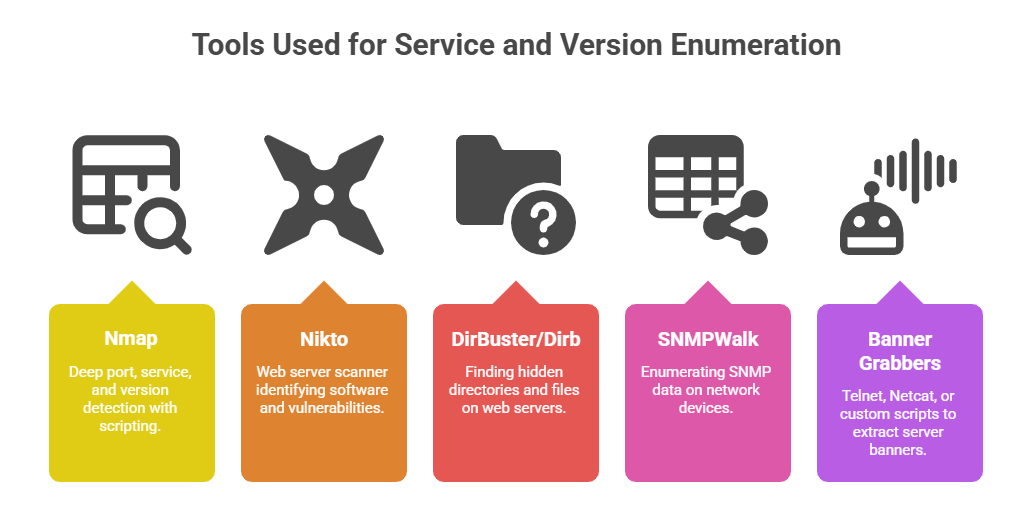
1. Probing Ports: Using tools like Nmap, Nessus, or specialised scripts to scan for open ports.
2. Banner Grabbing: Capturing banners—the textual information provided by servers—containing service and version details. This can be done through manual telnet sessions or automated tools.
3. Protocol-Specific Queries: Sending specific commands tailored for protocols like HTTP (GET, OPTIONS), FTP (LIST), SMTP (VRFY, EXPN), to gather detailed configuration and version information.
4. Web Application Enumeration: Using tools such as Nikto, Dirb, or Burp Suite to identify server software, web frameworks, and versions from HTTP headers and responses.
Key Techniques in Service & Version Enumeration
Here are some commonly used methods that aid in identifying service and version information:
1. Banner Grabbing: Connecting to a service and capturing banner messages that disclose software type and version.
2. TCP/IP Stack Fingerprinting: Analyzing responses from network stack implementation to identify OS and service versions.
3. Protocol Fuzzing: Sending crafted or malformed packets to trigger error messages revealing underlying software details.
4. Web Application Fingerprinting: Analyzing HTTP response headers, error messages, or page source to identify server software and versions.
 Best Practices and Considerations
Best Practices and Considerations
Maintaining a secure and ethical approach to enumeration involves adhering to industry-standard precautions. Listed here are important practices that strengthen the overall process:
1. Authorization: Ensure active enumeration is performed only with explicit permission to avoid legal and ethical violations.
2. Timing & Stealth: Use slow and randomized scan techniques to avoid detection and reduce impact on the target’s performance.
3. Regular Updating: Keep enumeration tools updated to recognize the latest software and vulnerabilities.
4. Post-Enumeration Actions: Use the gathered information to check for known vulnerabilities, misconfigurations, or outdated software.
Class Sessions
Sales Campaign

We have a sales campaign on our promoted courses and products. You can purchase 1 products at a discounted price up to 15% discount.
