Social engineering in cybersecurity refers to the psychological manipulation of individuals to gain confidential information, access, or other sensitive assets. Unlike purely technical hacking methods, social engineering exploits human behavior, emotions, and trust to bypass security controls.
Phishing is one of the most widespread social engineering techniques, where attackers impersonate trusted entities to deceive victims into sharing sensitive data such as passwords or financial information. Understanding these principles helps individuals and organizations better recognize and defend against such attacks.
What is Social Engineering?
Social engineering attacks rely on manipulating human psychology rather than technical vulnerabilities. Attackers use tactics that exploit trust, fear, urgency, curiosity, or helpfulness to convince victims to perform compromising actions.
These actions may include divulging credentials, clicking on malicious links, downloading malware, or providing physical access. Social engineering can occur over email, phone calls, text messages, social media, or in person.
Phishing
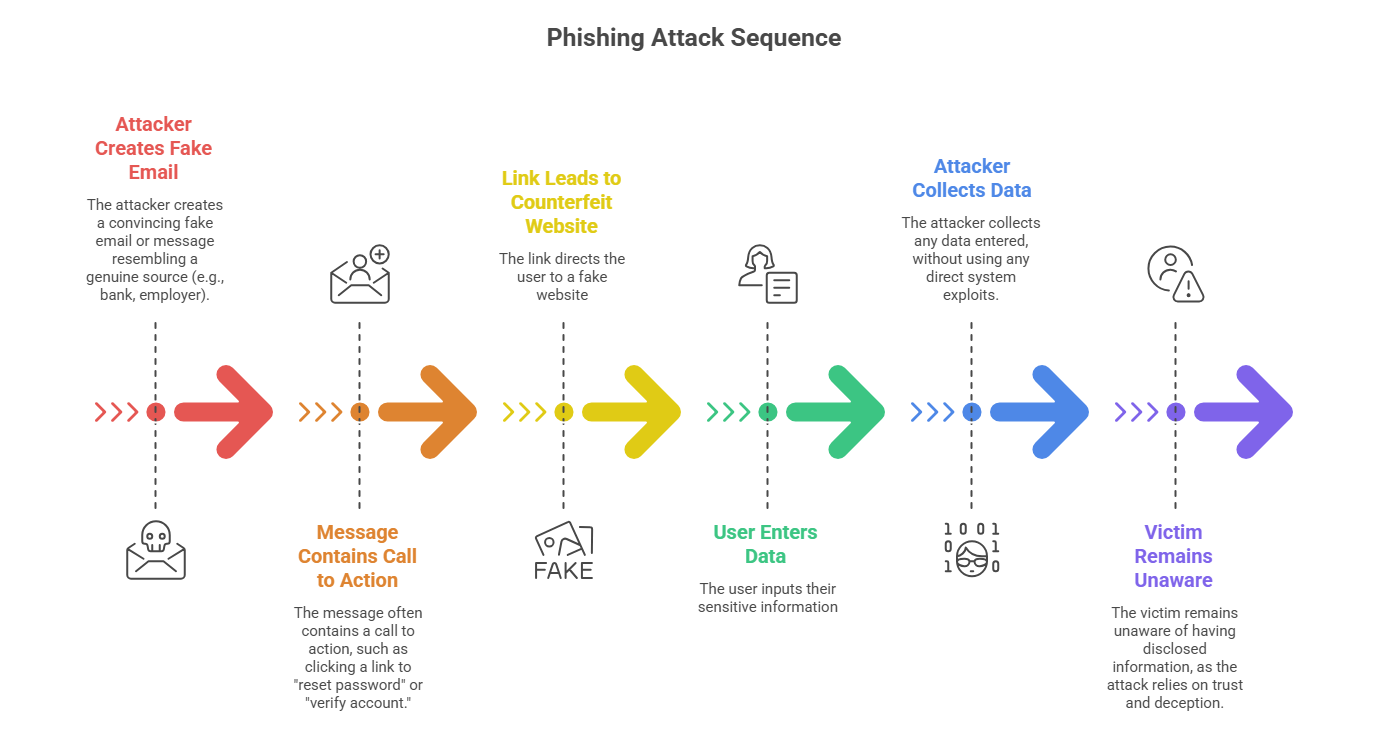
Phishing is a social engineering attack where an adversary impersonates a legitimate organization or person in electronic communications to lure victims into revealing sensitive information. Typical phishing methods include deceptive emails, fake websites, and messages with urgent requests or alarming content.
Variants Include:
1. Spear Phishing: Targeted attacks aimed at specific individuals or organizations using personalized information.
2. Vishing: Phishing conducted over voice calls.
3. Smishing: Phishing via SMS/text messages.
The goal is often to steal login credentials, financial information, or to deliver malware.
How Phishing Works
Why is Social Engineering Effective?
Social engineering is effective because attackers blend trust, urgency, and targeted research to influence decisions. The factors described here explain why individuals are often tricked despite technical safeguards:
1. Humans tend to trust familiar logos, domain names, and language.
2. Strong emotions like fear or urgency cause people to act quickly without reflection.
3. Lack of awareness or training about phishing increases susceptibility.
4. Social engineers research their targets to tailor messages, enhancing believability.
Preventing Social Engineering and Phishing
1. Provide regular training to users to recognize phishing indicators and suspicious communications.
2. Implement email filtering technologies to reduce spam and phishing emails.
3. Encourage verification of requests through alternative channels (e.g., phone call).
4. Use multi-factor authentication (MFA) to reduce risks from compromised credentials.
5. Maintain an organizational culture promoting skepticism and verification.
