In network security, firewalls and NAT (Network Address Translation) are crucial tools for controlling and securing data flow within and across networks.
Firewalls act as gatekeepers that monitor and filter incoming and outgoing traffic based on predefined security rules. NAT, on the other hand, helps manage IP address allocation and enhances security by hiding internal network details from external threats.
Firewalls
A firewall is a network security device or software designed to monitor, filter, and control traffic based on security policies. It acts as a barrier between a trusted internal network and untrusted external networks, such as the internet. Firewalls inspect packets of data to determine whether they meet security criteria before allowing them to pass.
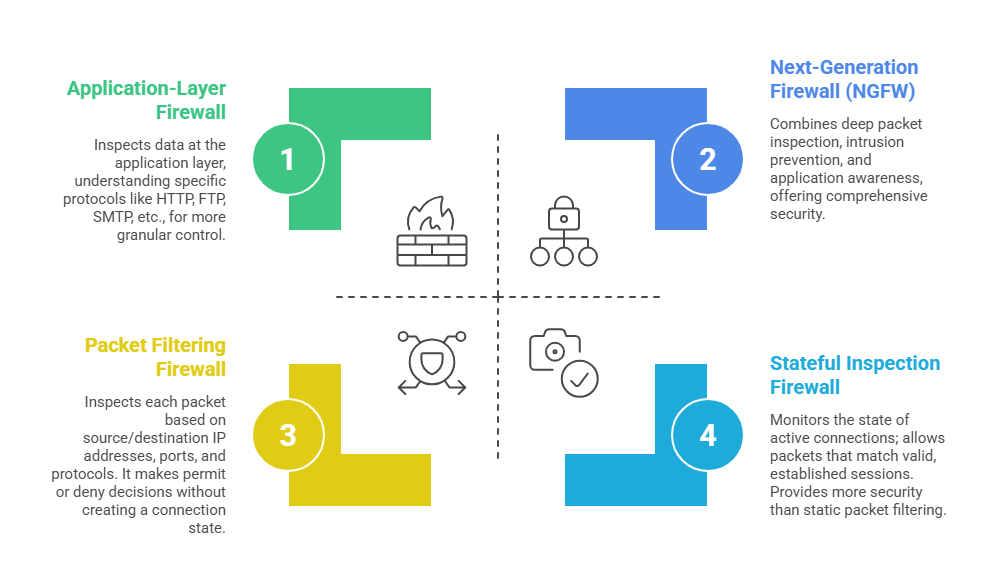
Types of Firewalls
Firewall Functions
Firewalls serve as the first line of defence, ensuring that only permitted traffic and users reach internal systems. The functions outlined here represent the core capabilities of a firewall:
1. Traffic Control: Allow, block, or restrict data flow based on rules.
2. Access Control: Restrict internal resources from unauthorised external access.
3. Monitoring & Logging: Record traffic attempts for security analysis and incident response.
4. Threat Prevention: Detect and prevent intrusion attempts, malware, and malicious payloads.
NAT (Network Address Translation)
NAT translates private IP addresses used within a local network to public IP addresses for communication over the Internet, and vice versa. It allows multiple devices within a LAN to share a single public IP address, conserving IP resources. NAT provides an additional layer of security by hiding internal IP addresses from external sources, making direct attacks more difficult.
Basic Packet Flow
Packet flow describes the sequence of actions that occur when data leaves a device, gets inspected, translated, routed, and finally delivered. Here are the key stages involved in this process:
1. Packet Generation: When a device sends data, it creates packets containing source IP, destination IP, source port, and destination port.
2. Packet Filtering by Firewall: The firewall inspects each packet’s header and compares it against security rules. Allowed packets proceed, while blocked packets are dropped or quarantined.
3. NAT Processing: If NAT is used, the packet’s source IP may be replaced with the firewall’s public IP address during outbound transmission. On return, the process is reversed.
4. Routing: Allowed packets are forwarded to their destination via routers, and responses follow the reverse path, passing through the firewall and NAT.
5. Delivery: The packets arrive at the destination, and responses follow the same process in reverse, maintaining security and traffic control.
Practical Considerations
Class Sessions
Sales Campaign

We have a sales campaign on our promoted courses and products. You can purchase 1 products at a discounted price up to 15% discount.
.png)
