The Cyber Kill Chain is a structured model that describes the stages of a cyberattack from the attacker's initial reconnaissance to achieving their intended objectives.
Developed by Lockheed Martin, this framework helps cybersecurity professionals understand and defend against intrusions by breaking down an attack into clear, manageable phases. Recognizing each phase enables defenders to detect, disrupt, and mitigate attacks before damage occurs.
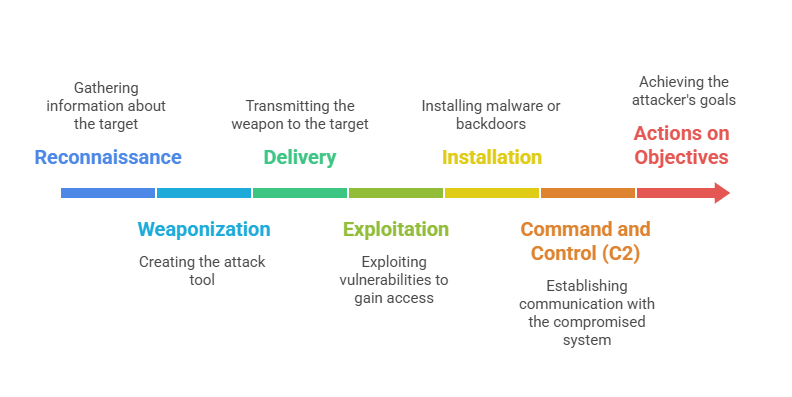
Seven Phases of the Cyber Kill Chain
By mapping attacker behaviors, the Cyber Kill Chain provides a structured approach for strengthening defenses. The seven phases outlined here illustrate how attackers plan, execute, and complete an intrusion:
1. Reconnaissance
This is the initial stage where attackers gather information about their target. They study the organization's network, systems, personnel, and potential vulnerabilities. Techniques include passive methods like open-source intelligence (OSINT) and active scanning to discover weaknesses. Effective reconnaissance allows attackers to develop a tailored attack strategy.
2. Weaponization
Once information is gathered, attackers build or customize malicious payloads such as malware or exploit kits. This phase combines a remote access malware with a delivery mechanism (e.g., phishing email) tailored for the target’s vulnerabilities. Weaponization prepares the tools needed to launch an attack.
3. Delivery
In this phase, attackers transmit the malicious payload to the target system. Common delivery methods include phishing emails, malicious attachments, infected websites, or exploiting open network ports. The goal is to insert the weaponized payload into the victim's environment.
4. Exploitation
Upon delivery, attackers exploit vulnerabilities to execute malicious code. This step often leverages software bugs, misconfigurations, or user errors. Successful exploitation gives the attacker unauthorized access to the target systems.
5. Installation
After exploiting the target, malware or backdoors are installed to maintain persistence. This allows attackers to retain access even if the initial vulnerability is patched or detected, enabling long-term presence within the network.
6. Command and Control (C2)
Attackers establish communication channels to remotely manipulate compromised systems. Through C2 servers or protocols, they instruct malware or infected machines to carry out further actions, receive data, or expand control.
7. Actions on Objectives
This final stage involves achieving the attack’s primary intent, such as data theft, system disruption, data encryption for ransom, or sabotage. The attacker uses their foothold to fulfill objectives that can have significant operational or financial consequences for the target.
Class Sessions
Sales Campaign

We have a sales campaign on our promoted courses and products. You can purchase 1 products at a discounted price up to 15% discount.