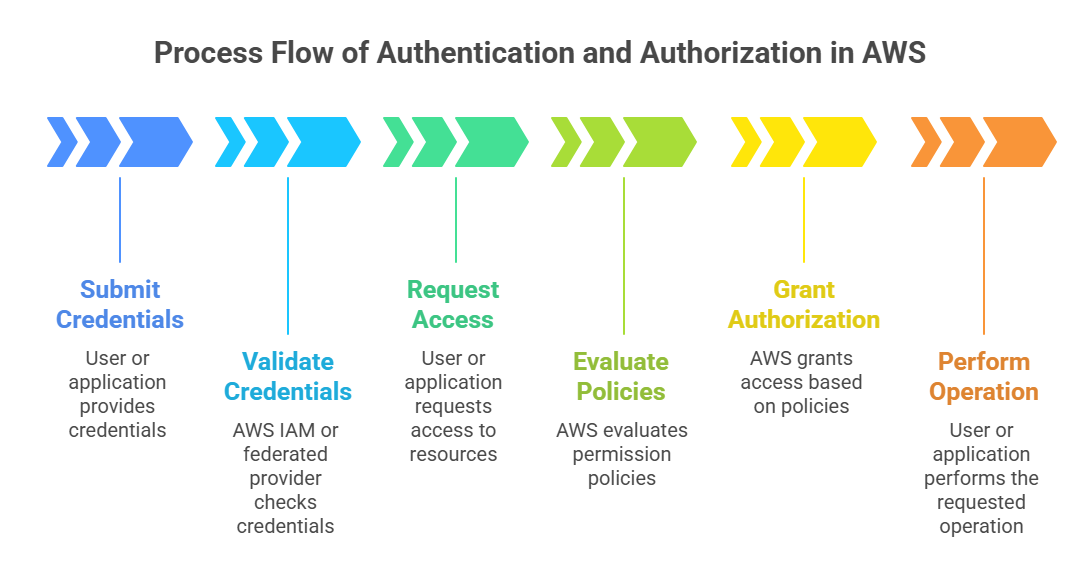
Authentication and authorization are foundational concepts in securing cloud environments and applications. Authentication is the process of verifying the identity of a user, system, or service, ensuring that they are who they claim to be.
Authorization, on the other hand, determines what authenticated identities are allowed to do—defining permissions and access levels to resources and services.
Together, these processes protect sensitive data, maintain compliance, and prevent unauthorized actions.
In AWS, Identity and Access Management (IAM), alongside services like Amazon Cognito, provide the mechanisms to manage authentication and authorization effectively.
Authentication
Authentication confirms the identity of an entity — typically by credentials such as usernames and passwords, access keys, or tokens. AWS supports multiple authentication methods:
1. IAM Users and Roles: IAM manages identities within AWS, allowing creation of users and roles that define how human operators or applications authenticate to AWS resources.
2. Federated Authentication: Supports enabling single sign-on (SSO) and identity federation with external identity providers such as Microsoft Active Directory, Google, or Facebook via standards like SAML and OAuth.
3. Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring a second verification method (e.g., a smartphone app-generated code) in addition to a password.
4. Amazon Cognito: Provides user directory services, authentication, and user management specifically designed for web and mobile applications, including social identity federation.
Authorization
Once an identity is authenticated, authorization decides the actions it can perform within the AWS environment. AWS authorization is primarily controlled through IAM policies, which are JSON-based documents defining permissions.
Key Authorization Components Include:
1. Identity-Based Policies: Attached directly to users, groups, or roles specifying allowed or denied AWS API actions on resources.
2. Resource-Based Policies: Policies attached to AWS resources, such as S3 buckets or SQS queues, to specify who can access them.
3. Permission Boundaries and Service Control Policies: Provide additional layers of permissions management at organisational or role levels.
4. Least Privilege Principle: Best practice aiming to grant only the minimal required permissions necessary for tasks to minimise security risks.
Security Best Practices
1. Use IAM roles with temporary security credentials for applications rather than long-term access keys.
2. Enforce MFA, especially for sensitive operations or root accounts.
3. Regularly review and audit permissions to avoid privilege creep.
4. Use fine-grained policies to tightly control access.
5. Leverage Amazon Cognito for user-facing application authentication and federated identity.
Class Sessions
Sales Campaign

We have a sales campaign on our promoted courses and products. You can purchase 1 products at a discounted price up to 15% discount.
